60% of Employees Say They Ignore or Get Around Workplace AI Rules, Report Finds
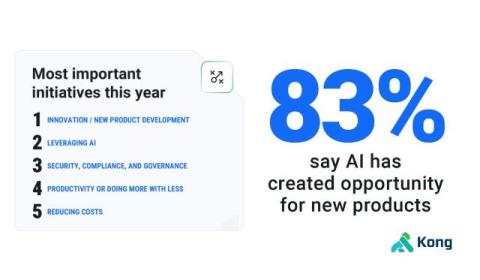
What do developers really think about artificial intelligence (AI)? To many, AI is synonymous with innovation. While some noisy naysayers on the sidelines may cry the promise of generative AI (GenAI) is overhyped, the reality experienced by actual developers and leaders in the digital trenches working with GenAI and large language models (LLMs) tells a clear story: AI is a top priority in the enterprise today because it has already delivered real, tangible business benefits.