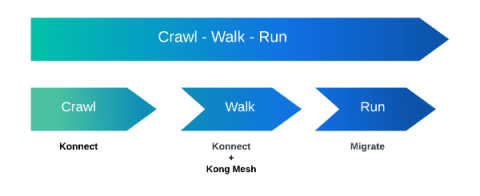
Kong Spring Update: The Blossoming Season
We started 2023 by closing our fiscal year and achieving hypergrowth — once again. We’ve surpassed 600 customers, increased our employee base by 22% year over year, opened our newest office in Singapore following rapid growth in the Asia Pacific region, and expanded meetups to 46 countries and more than 12,000 attendees.