Systems | Development | Analytics | API | Testing
Security
Why an Integrated Approach to Data and Cybersecurity Critical for CXOs
In the digital age, where data is often regarded as the new oil, businesses are responsible for safeguarding their most valuable asset – Information. Data breaches, cyberattacks, and vulnerabilities have surged to unprecedented levels, prompting organizations to invest significantly in bolstering their defenses. Cybersecurity statistics reveal a staggering rate of 2,200 cyber attacks occurring daily, with a new attack occurring approximately every 39 seconds.
Choosing the Right Host for SFTP: Factors to Consider
Security and risk mitigation in an LLM world
We’ve talked about the many ways large language models (LLMs) and artificial intelligence (AI) are impacting business efficiency, data and analytics, and even FinOps. But we’ve yet to talk about arguably one of the most important areas of concern: security.
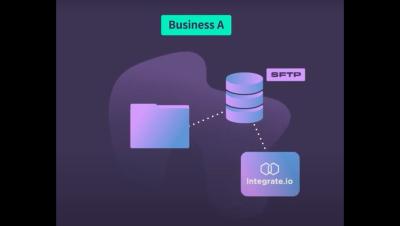
Integrate.io's SFTP Integration Explained
Why Website Security is Important for your Business?
Options for passwordless authentication in Django apps
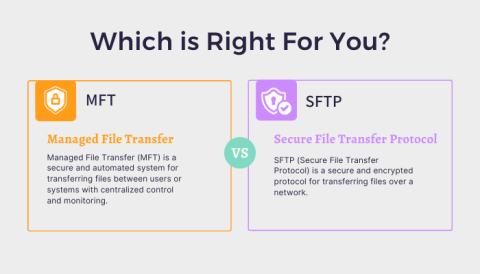
MFT vs. SFTP: Which File Transfer Is Right for You?
Strengthening Your Data Ecosystem with Unrivaled Security
As data ecosystems evolve security becomes a paramount concern, especially within the realm of private cloud environments. Cloudera on Private Cloud with the Private Cloud Base (CDP PvC Base) stands as a beacon of innovation in the realm of data security, offering a holistic suite of features that work in concert to safeguard sensitive information.