Systems | Development | Analytics | API | Testing
December 2020
Automating Contract-Centric Experiences to Accelerate Front End Development
Comcast's Self-Service API Gateway Development Journey
Collaborative API Design and Testing with Insomnia
Communication Design Patterns for Microservices
Day 0 to Day 2 With Kuma, Helm and Kubernetes | FinTech Studios
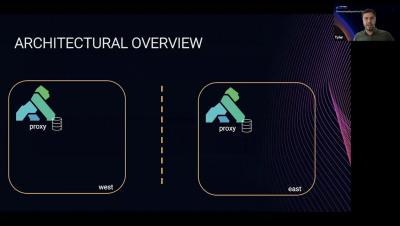
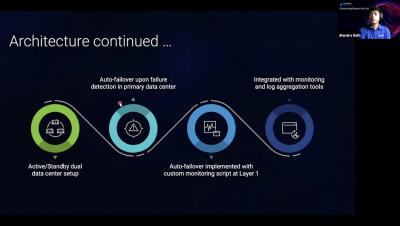
Considerations for Deploying a Multi-Cloud Architecture with Kong Gateway, Kuma Service Mesh and Aviatrix
Building a multi-region or multi-cloud environment for your applications requires a lot of attention. In a typical deployment, you would have an API gateway running close to the several application runtimes. You should enhance your deployment to support different regions in a given cloud, or in an even more distributed and hybrid scenario, multiple services running across other public clouds and on-premise environments.
Decentralizing API Design at NAB | National Australia Bank
Deploy With Ease and Enable API Automation With Scale
Kong Launches Kong Enterprise on Top Cloud Marketplaces
I’m excited to announce that Kong Enterprise, our modern, scalable service connectivity platform, is now available on top cloud marketplaces, including AWS Marketplace and GovCloud (US) regions, Azure Marketplace, Google Cloud Platform, and Red Hat Marketplace!
JWT Claims With Rate Limiting in Kong
In Kong, plugins can be thought of as policy enforcers. In the case of rate limiting, Kong offers two plugins: An open source one and Enterprise. Both plugins can limit requests per consumer, route, service or globally. Configuring the same plugin is also possible on a more than level. When this occurs, an order of precedence is used to determine which configuration to run. With this capability, it is possible to apply fine-grained policy control. In this article, we cover an advanced use case.
Enter the Next Level: Migrating to Cloud Native Platform
Distributed Multi-Cloud and Multi-Cluster Service Mesh | Kong Mesh
From Zero to Hero: A Roadmap for Automating the Dev Lifecycle Across Any Environment with GitOps
How Organizations Can Leverage Kubernetes as a Universal Computing Standard
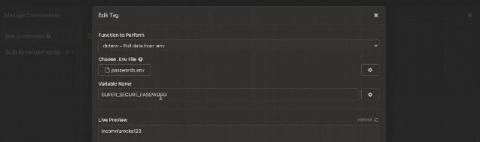
3 Solutions for Avoiding Plain-Text Passwords in Insomnia
When testing APIs, software engineers often repeat identical values across multiple requests, but who wants to waste time typing the same values every time? Insomnia’s environment variables solve this problem by allowing you to define a value once as an environment variable and reference that value wherever it’s needed. Insomnia also enables you to override certain variables using sub-environments or folder environments.
How Papa John's Fast-Tracked External API Innovation With Kong
How to Achieve Zero-Trust Security With Service Mesh | Kong Summit 2020
How to Migrate an Existing Application to Serverless | AWS
Infrastructure and Software Development: What Got Us Here Won't Get Us There
Kong Enterprise From the Trenches: Real-World Challenges and Lessons Learned
Introducing gRPC Support for Insomnia
We’re happy to announce the release of gRPC support for Insomnia, now available in the 2020.5 release. With gRPC support, developers can make requests to gRPC backend services just like they can today with REST / GraphQL services from Insomnia.
How to Set Up Kong Gateway
You’ve decided to install Kong Gateway. Congrats! You’re almost ready to accelerate your microservices journey with the world’s most popular open source API gateway. This article and video will guide you through the short version of our tutorial. If you prefer, here are some more detailed instructions. If you haven’t already, make sure you’ve installed Kong before getting started. It should only take a few minutes.