Systems | Development | Analytics | API | Testing
Networks
Exploring Various Protocols : Http To Databases
Empowering Transactions Beyond Networks: The Future and Security of Offline Payments in a Digital Era
On many occasions, your mobile phone may be out of network coverage. Or you may be traveling in a remote area without network connectivity. In this digital era, don’t you think you should be given the option to pay digitally in such situations, even when there is a network issue? Being able to pay digitally is far better than the need to carry cash for payments, but that is a separate topic on which we can have a particular blog later.
Zero Trust Network Access (ZTNA) vs VPNs
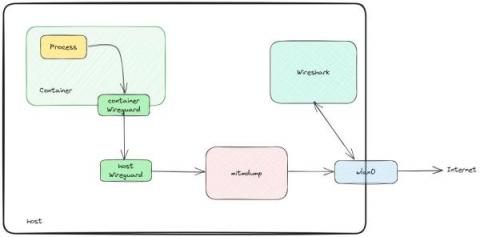
Inspect TLS encrypted traffic using mitmproxy and wireshark
I had the chance to finally sit down and find a way to inspect TLS traffic flowing out of an application running on my machine. Although I did not invent anything, I needed to put together a lot of different tricks in order to succeed, and the documentation I could find online regarding this process is scattered, at best. So, here we are with a guide on “how to inspect TLS encrypted traffic without going nuts”. Hope you enjoy!
Testing Kubernetes networking with k6 - Roberto Santalla (k6 Office Hours #91)
IP Geofencing With Methodics IPLM
IP geofencing should be a central part of your IP strategy. Why? Because your IP portfolio is probably leaking. And IP leakage can cost millions of dollars in lost revenue and market setbacks — not to mention export violation fines. When it comes to IP security, you need a three-pronged approach: This blog will focus on the first pillar listed above: IP geofencing. Talk to a GEOFENCING Expert.
VPCs: An Introduction to Secure Business Networking
Key choices in AWS network design: VPC peering vs Transit Gateway and beyond
This blog post is the first in what we intend to be a series to detail Ably’s journey in building the next iteration of our global network. It focuses on the design and we will follow up with posts detailing the building, and finally migration from old to new. If you are interested in how you can network AWS accounts together on a global scale then read on! Ably operates a global network spanning 8 AWS regions with hundreds of additional points-of-presences.
Telco 5G Returns Will Come from Enterprise Data Solutions
Communications service providers (CSPs) are rethinking their approach to enterprise services in the era of advanced wireless connectivity and 5G networks, as well as with the continuing maturity of fibre and Software-Defined Wide Area Network (SD-WAN) portfolios.