Systems | Development | Analytics | API | Testing
June 2024
Amber Electric Relies On The AI Data Cloud To Give Australians Greater Control Of Their Energy Usage
Amber Electric is on a mission to help shift Australia to 100% renewable energy. They are powered by a desire to show people that a win for the planet is a win for them too. The Snowflake AI Data Cloud has proven to be a hit at Amber Electric thanks to its easy-to-use interface, cost effectiveness, and scalability, helping the company streamline its customer invoicing and, as a result, customer experience.
Building AI With Ollama and Django
If you’re not building with AI, are you even building these days? Sometimes, it seems not. AI has become such an integral part of workflows throughout many tools that a clear understanding of integrating it into your product and framework is critical. Django is such a framework that powers thousands of products across the web: Instagram, Pinterest, and Mozilla are all services built on Django.
Mastering Access Control Allow Origin: Your Guide to Secure Cross-Domain Requests
Understanding and configuring the Access-Control-Allow-Origin header is critical for developers managing cross-domain requests. In this blog, we will look at setting the right headers to enforce security while allowing data exchange between different domains, including handling cross-domain requests as specified by the CORS specification. Prepare to equip yourself with the tools to implement cross-origin resource sharing effectively.
Fivetran Managed Data Lake Service Demo: Landing Data in S3 with Iceberg
To learn more about the Fivetran Managed Data Lake Service visit:
https://www.fivetran.com/data-movement/data-lakes
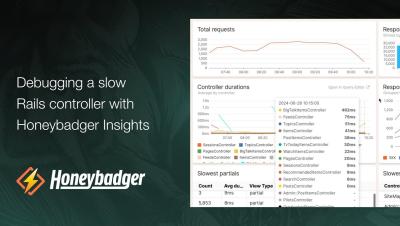
Debugging a slow Rails controller with Honeybadger Insights
Join Honeybadger cofounder Ben Curtis as he uses Honeybadger Insights to debug a slow controller action in Rails. Honeybadger Insights is a new full-stack logging, observability, and performance monitoring tool from Honeybadger.io. Gain insights into your errors, application logs, and other event streams with a powerful query language and ready-made dashboards.
Confluent Is Named Microsoft's 2024 OSS on Azure Global Partner of the Year
Confluent is thrilled to be named Microsoft’s 2024 OSS on Azure Global Partner of the Year. As a three-time Partner of the Year award winner, this recognition reflects our commitment to delivering outstanding open source-based applications and infrastructure solutions on Microsoft Azure.
Amazon OpenSearch Ingestion Adds Support for Confluent Cloud as Source
Until recently, customers didn't have an easy way to send data from Confluent’s data streaming platform to Amazon OpenSearch. They had to either write custom code using AWS Lambda as an intermediary, refactor the HTTP Sink connector, or self-manage an old Elasticsearch connector version. Earlier this year, we announced the fully managed OpenSearch Sink connector, providing a seamless way to sink data from Confluent to Amazon OpenSearch.
Understanding the difference between Virtual Users and Requests Per Second (RPS)
Hey there! If you’ve ever been curious about performance testing, you’ve probably come across the terms “Virtual Users” and “Requests Per Second (RPS)”. They might sound a bit technical, but they’re super important for ensuring your website or application runs smoothly, especially under heavy traffic. In this article, we’re going to break down what these terms mean, how they differ, and why they’re essential.
Fivetran at Snowflake Summit 2024: Key takeaways
From announcing the release of Managed Data Lake Service and Native App development to customer sessions with BlackRock and Honeywell.
From Checkout Chaos to Seamless Transactions: The Power of Automated POS Testing
In the busy world of retail, the checkout process is the last and often most crucial step in the customer journey. A smooth, efficient transaction can leave a lasting positive impression, while any hiccup can lead to frustration, abandoned carts, and lost sales. With the rise of advanced Point-of-Sale (POS) systems, retailers have more tools than ever to streamline operations and improve the customer experience.
3 Powerful Extensions to Improve Security and Get the Most Out of Kong
OAuth 2.0 is the current gold standard for secure delegated authorization. The reason is simple: OAuth puts control back in the hands of the users. It enables users to securely grant access to their resources without having to share passwords with third-party applications. Hence, it's one of the most widely adopted standards in the industry.